When was the last time your organization reviewed its authentication strategy against current standards? If it was before July 2025, you're likely missing critical updates from NIST SP 800-63, Revision 4 that affect compliance and security posture.
Released last summer after nearly four years of development and approximately 6,000 public comments, as reported in the NIST blog, this update replaces the 2017 SP 800-63-3 standards. These aren't just federal guidelines. They influence regulatory frameworks across banking, insurance, healthcare, and government contracting. Organizations that haven't assessed their systems against these requirements may face compliance gaps during their next audit.
Critical Changes to be Aware of (and Address)
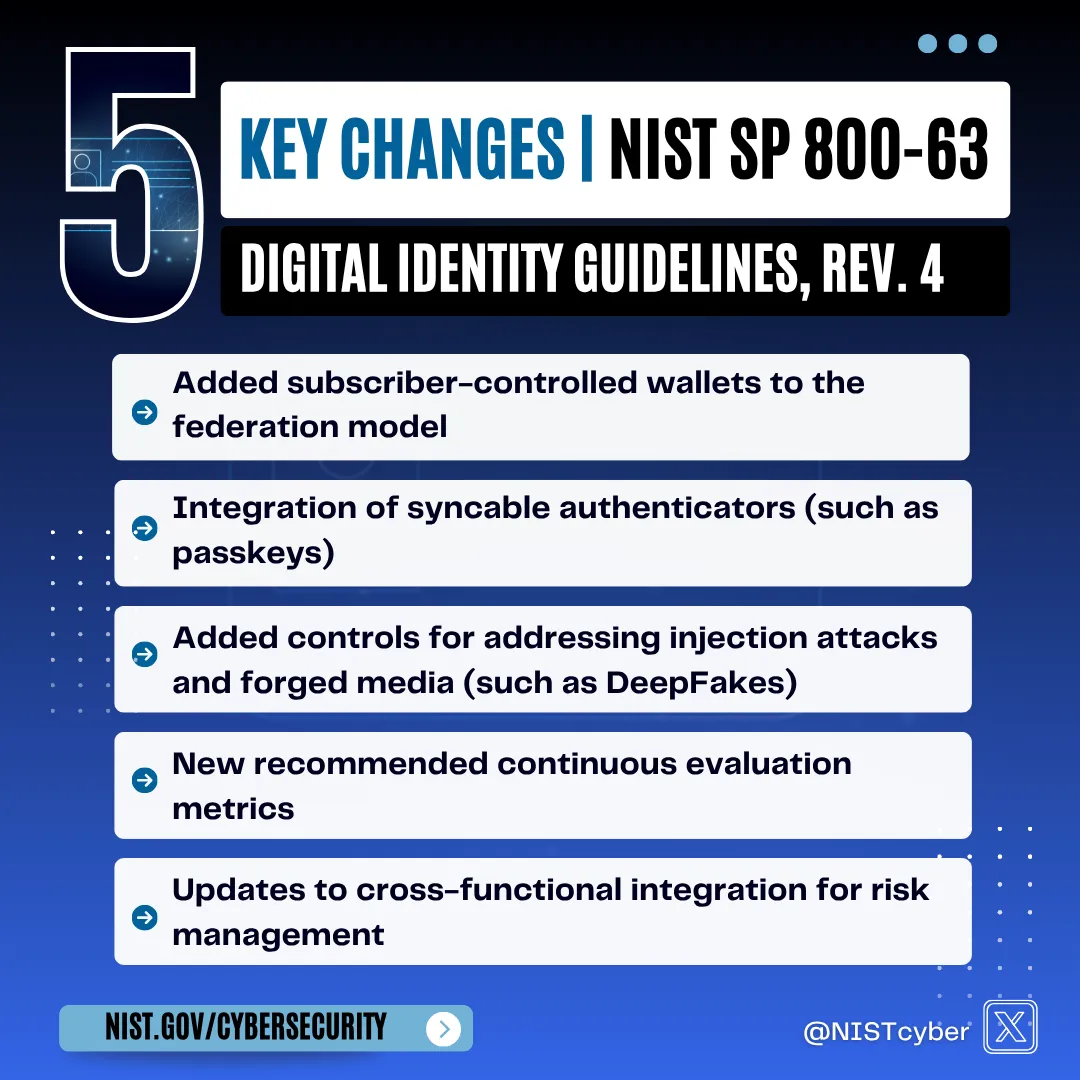
Three changes from last year's update demand attention if you haven't already addressed them:
- IAL1 now targets synthetic identity fraud at scale. The updated Identity Assurance Level 1 specifically addresses bot-driven account creation and fake identity attacks. If you're onboarding customers digitally, your processes may no longer meet the baseline.
- Phishing-resistant authentication becomes the standard. The new Authentication Assurance Levels require organizations to evaluate whether password-based systems still provide adequate protection. This affects everything from employee access to customer portals.
- Identity management becomes cross-functional. NIST explicitly requires collaboration between cybersecurity, privacy, legal, customer experience, and business units. Organizations that treat identity as solely an IT concern will struggle to implement these guidelines effectively.
Identity as Infrastructure, Not a Feature
As infrastructure continues to shift toward cloud-native, distributed models, identity becomes an operational control point, not just a front-end requirement. Whether you’re managing Kubernetes clusters, PostgreSQL databases, CI/CD pipelines, or cloud APIs, how users and services authenticate, authorize, and federate directly impacts operational security.
The framework operates on three independent assurance dimensions:
- Identity Assurance Level (IAL) establishes confidence in a user's real-world identity, from basic attribute validation at IAL1 through in-person biometric proofing at IAL3.
- Authentication Assurance Level (AAL) measures confidence that the authenticating party is the authorized subscriber, ranging from single-factor at AAL1 to phishing-resistant cryptographic authentication at AAL3.
- Federation Assurance Level (FAL) governs assertion strength when identity providers pass claims to relying parties.
Organizations can calibrate these independently. A public information portal might need strong authentication (AAL2) without identity proofing. A loan application requires both robust proofing (IAL2) and authentication (AAL2).
Learn more about Control Points in this White Paper on Service Monitoring via Hazard Analysis
The Digital Identity Risk Management Process
NIST now mandates a structured approach called Digital Identity Risk Management (DIRM). This isn't optional. Organizations must document their decisions in a Digital Identity Acceptance Statement, following five steps:
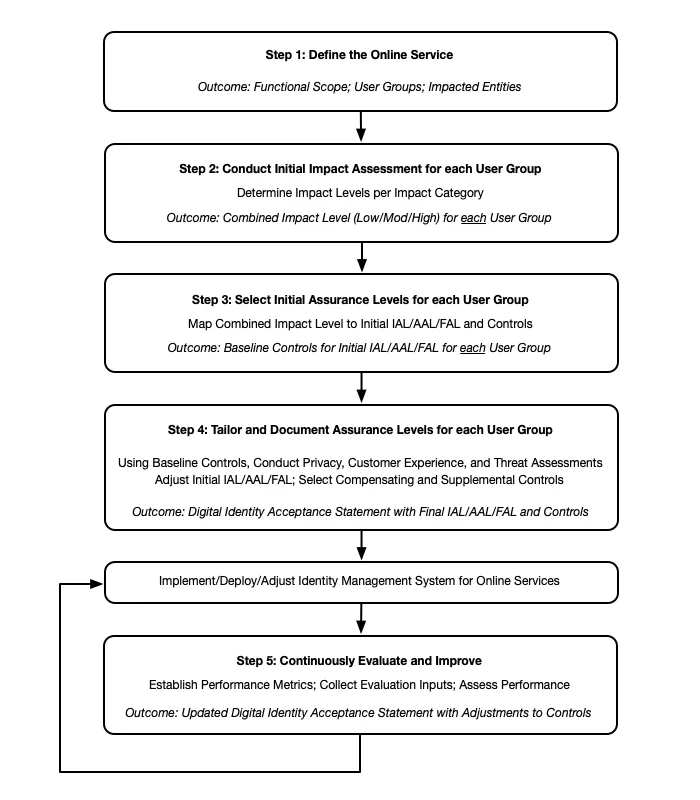
- Define your online service by documenting functionality, user groups, data processed, and affected stakeholders.
- Conduct an initial impact assessment across categories, including inconvenience, distress, financial loss, and organizational harm.
- Select initial assurance levels based on impact determinations.
- Tailor those levels by assessing privacy impacts, fraud resistance, customer experience, and equity considerations.
- Implement continuous evaluation using metrics like authentication failure rates, confirmed fraud incidents, and customer satisfaction data.
This structured process forces explicit decisions about security trade-offs and creates an audit trail for compliance reviews.
What This Means for Your Organization
The scope of SP 800-63-4 extends beyond federal agencies. Organizations in regulated industries should treat these guidelines as the baseline for identity assurance. Here's what requires assessment if you haven't already addressed it:
- Current authentication flows. Review whether your existing systems meet the new AAL requirements, particularly around phishing resistance.
- Identity proofing processes. Evaluate whether customer onboarding aligns with updated IAL controls and addresses synthetic identity fraud.
- Federation configurations. For organizations using SSO or identity federation, assess whether assertion protocols meet FAL standards.
- Cross-functional coordination. Identity risk management now explicitly requires input from legal, privacy, security, customer experience, and business stakeholders. Siloed IT implementations won't satisfy the new framework.
- Continuous monitoring capabilities. The requirement for ongoing metrics means organizations need systems to track authentication failures, fraud indicators, and customer experience data.
Implementation Considerations
Organizations beginning their assessment should audit current identity controls against the new framework. This means mapping existing authentication methods to AAL requirements, evaluating identity proofing procedures against IAL standards, and documenting gaps in federation security.
The guidelines support emerging technologies, including mobile driver's licenses and verifiable credentials. Organizations planning identity system upgrades now have a standards-based roadmap for implementation.
Password requirements have also evolved, moving away from rigid composition rules (no more "must contain special character" mandates) toward approaches that emphasize length and screening against compromised credential databases.
Need help implementing secure processes and environments?
At Command Prompt, we work with organizations that need more than just secure databases. They need a trusted infrastructure that supports compliance, performance, and operational excellence.
That means understanding how identity controls integrate with PostgreSQL deployments, how access patterns affect database security, and how authentication flows impact system architecture.
We can help you:
- Assess your current authentication and access controls
- Align PostgreSQL deployments with NIST SP 800-63 assurance levels
- Implement rate limiting, role-based access controls, and comprehensive audit logging
- Integrate identity-aware infrastructure into your DevSecOps workflows
Reach out to discuss how we can help you design and deploy secure authentication protocols and build systems that meet the latest standards while maintaining an ideal user experience.
Learn more: Take a deep dive into the NIST SP 800-63-4 Guidelines publication and its companion volumes — [SP800-63A], [SP800-63B], and [SP800-63C] — which provide technical and process guidelines to organizations for the implementation of digital identity services.
